The Evolution of the Access Card and Its Significance to Safety and Security!
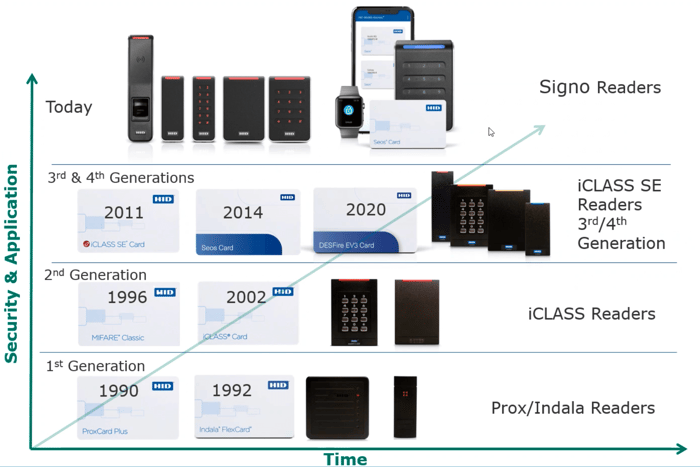
The Access Card have been a pinnacle of physical security for decades, providing a reliable method for controlling entry to buildings, facilities, and restricted areas. As security threats have evolved, so too have access cards, advancing from simple magnetic stripes to highly encrypted, nearly impossible-to-clone smart cards. This progression has greatly enhanced safety, ensuring that only authorized individuals can gain entry to sensitive locations. 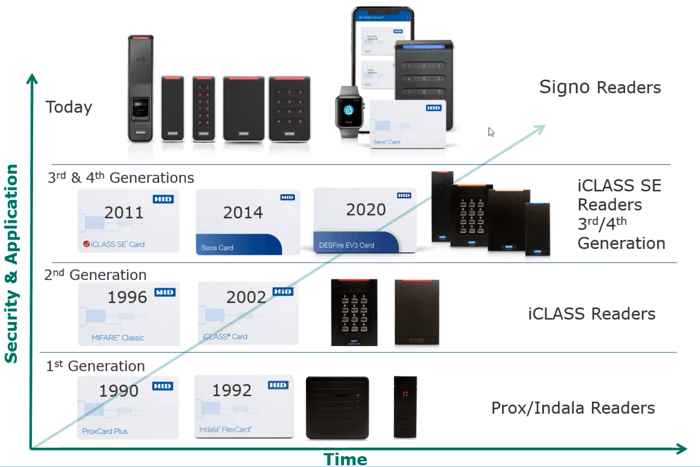
The Early Days: Magnetic Stripe and Proximity Cards
In the 1970s and 1980s, magnetic stripe cards became widely used for access control. These cards stored credential data on a magnetic strip, much like credit cards. While revolutionary for their time, they had significant security weaknesses. The data stored on these cards was static, making them easy to clone with relatively inexpensive devices. This posed a major security risk, as a lost or stolen card could be duplicated and misused without detection.
The next evolution was the introduction of proximity (prox) cards, which utilized radio frequency identification (RFID) technology. Prox cards enabled contactless entry and improved convenience, but they still lacked encryption, making them vulnerable to cloning. Anyone with the right tools could intercept and replicate the signal, allowing unauthorized individuals to create duplicate access cards.
Advancements in Encryption: Smart Cards and HID Seos
Recognizing the vulnerabilities of traditional access cards, security manufacturers developed smart cards, which introduced encryption and mutual authentication between the card and reader. Unlike proximity cards, smart cards store encrypted data on embedded microchips, requiring more sophisticated technology to access or replicate the information.

A major advancement in this field is HID Global’s Seos technology, which utilizes advanced encryption and secure communication protocols. Seos cards eliminate many of the weaknesses found in legacy systems by using highly secure data transmission methods that prevent cloning or hacking attempts. The information on these cards is encrypted, ensuring that each transaction is unique, making replication virtually impossible.
The Role of Mobile Credentials in Access Control
As Access technology continues to evolve, mobile credentials are becoming an increasingly popular alternative to physical access cards. These credentials leverage smartphones and wearable devices to grant access via encrypted communication, such as Bluetooth or NFC (Near Field Communication). Since smartphones incorporate biometric authentication methods like facial recognition and fingerprint scanning, they add an extra layer of security beyond what traditional access cards offer.
Mobile credentials also provide flexibility and convenience for security teams, allowing remote credential management, instant revocation of access, and seamless integration with enterprise security systems. Organizations that implement mobile access solutions benefit from reduced risks of lost or stolen cards while enhancing user convenience.
The Future of Access Control: Multi-Factor Authentication and AI Integration
The future of access control is heading toward multi-factor authentication (MFA), where access credentials are combined with additional layers of verification, such as biometrics, PIN codes, or behavioral authentication. Artificial intelligence (AI) is also playing a role in enhancing security by detecting anomalies in access patterns and automatically flagging suspicious activity.
With cyber and physical threats continuously evolving, organizations must stay ahead by adopting access solutions that are encrypted, resilient, and secure against cloning. The transition from basic magnetic stripe cards to highly encrypted smart cards and mobile credentials represents a significant leap in safeguarding facilities, assets, and people from unauthorized access.
Conclusion
The evolution of access cards has been driven by the need for stronger security and protection against unauthorized duplication. From the early days of magnetic stripe and prox cards to today’s highly secure encrypted smart cards and mobile credentials, access control technology has advanced tremendously. As organizations continue to prioritize safety, investing in the latest encrypted access control solutions is critical for ensuring a secure and efficient security infrastructure.
By leveraging advanced encryption, smart authentication methods, and AI-driven security systems, businesses and institutions can stay ahead of potential threats and safeguard their environments with confidence.